Solana to Ethereum: The Trail of a High-Stakes Crypto Theft
The notorious Lazarus Group, linked to North Korea’s regime, has struck once again—this time pulling off a $3.2 million digital asset heist that started on May 16 and has sent ripples through the crypto community.
On-chain sleuth ZachXBT was first to connect the dots, revealing that the hackers targeted a user’s Solana wallet, converted the stolen funds into Ethereum, and funneled 800 ETH into Tornado Cash, the infamous crypto mixer used to obscure digital trails. At present, about $1.25 million remains unlaundered, sitting in an Ethereum wallet holding both DAI and ETH.
The method was surgical: quick conversions, privacy protocol usage, and sophisticated laundering. But this is only one part of a much bigger campaign Lazarus has been executing.
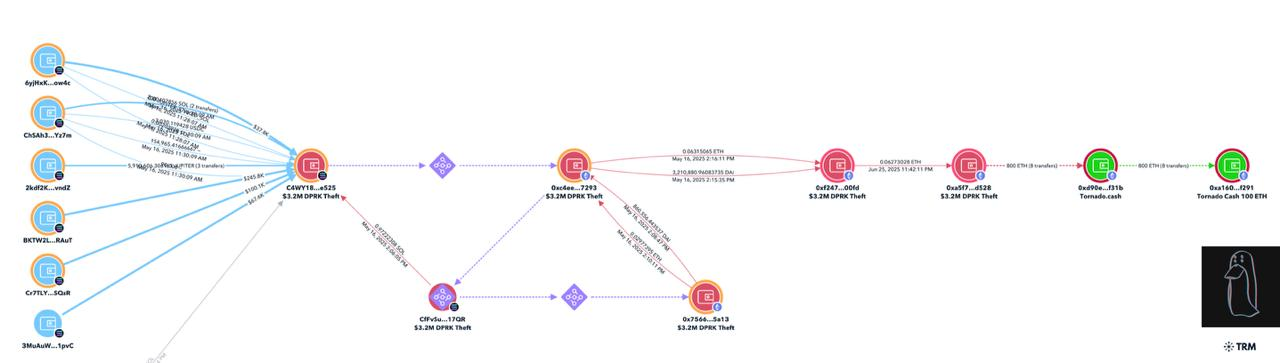
Lazarus Transactions Map | Source: ZachXBT
NFT Exploits and Targeted Dev Infiltration
Just two days before the Solana theft was revealed, ZachXBT uncovered another major breach involving multiple NFT projects, including those linked to Pepe creator Matt Furie, as well as ChainSaw and Favrr.
That attack began June 18, when Lazarus hackers gained control of several NFT contracts, proceeded to mint and dump tokens, and made off with another $1 million. The attackers shuffled the funds through three Ethereum wallets, converted some into stablecoins, and moved the assets to MEXC, a centralized crypto exchange.
ZachXBT noted that a specific MEXC deposit address reappeared across several incidents, pointing to repeat laundering behavior and connections to multiple scam projects. This isn’t just a hit-and-run - it’s a coordinated digital crime spree with layers of obfuscation and complex operational structure.
1/ Multiple projects tied to Pepe creator Matt Furie & ChainSaw as well as another project Favrr were exploited in the past week which resulted in ~$1M stolen
— ZachXBT (@zachxbt) June 27, 2025
My analysis links both attacks to the same cluster of DPRK IT workers who were likely accidentally hired as developers. pic.twitter.com/85JRm5kLQO
1/ Multiple projects tied to Pepe creator Matt Furie & ChainSaw as well as another project Favrr were exploited in the past week which resulted in ~$1M stolen
— ZachXBT (@zachxbt) June 27, 2025
My analysis links both attacks to the same cluster of DPRK IT workers who were likely accidentally hired as developers. pic.twitter.com/85JRm5kLQO
Fake Developer Profiles and North Korean Footprints
Perhaps the most chilling part of the Lazarus strategy is their infiltration tactics. ZachXBT discovered GitHub accounts with Korean language settings, VPN usage logs pointing to Astral VPN, and Asia/Russia time zones - all in developers who claimed to be based in the U.S. One example stood out:
In one especially alarming case, Alex Hong, listed as the CTO of Favrr, is now believed to be a North Korean IT worker posing under a false identity. His LinkedIn profile has been deleted, and no verifiable work history remains, suggesting deliberate obfuscation and possible recruitment into Lazarus’s crypto subversion network.
Lazarus Expands Its Crypto Warfront
These attacks are not isolated. They're part of an ongoing, state-sponsored cyber warfare campaign. According to TRM Labs, North Korea-linked actors, including Lazarus, are responsible for stealing nearly $1.6 billion in crypto this year alone - 70% of all stolen assets in 2025.
The shift in tactics is clear: phishing is no longer the only weapon. Now it’s developer impersonation, GitHub account manipulation, and social engineering - executed with military-grade precision.
The end goal? Funding North Korea’s regime while destabilizing global crypto markets and exposing systemic vulnerabilities in blockchain infrastructure.
Urgent Calls for Industry Action
With Lazarus’s fingerprints on multi-million dollar hacks, industry analysts are warning crypto platforms to enhance their developer vetting, monitor unusual wallet behavior, and bolster on-chain analytics. The rise in developer infiltration and contract compromise poses a major threat - not just to investors, but to the integrity of decentralized ecosystems.
As the line between cybercrime and geopolitics blurs, one thing is certain: crypto security isn’t just a tech issue anymore - it’s national defense.



